NIS2: Supply chains and IT security
Regulation & EU Requirements - Reading time: 11 Min

In the depths of the digital world lurk invisible dangers that can threaten companies of all sizes and industries alike. The NIS2 Directive introduces important requirements for operators of critical infrastructure and key assets to strengthen cyber security. The implementation of these measures is particularly important for companies in important sectors to effectively arm themselves against cyber threats. The German Federal Office for Information Security (BSI) is playing a key role in helping companies comply with the NIS2 Directive. In our blog post on the NIS2 Directive, we provide you with a comprehensive overview of current developments, including the German implementation and its current status, as well as the requirements in the area of cyber security. The directive marks a significant step towards strengthening digital security in Europe and affects companies across all industries. Find out how you can effectively prepare your company for the challenges ahead and successfully implement the requirements of the directive.
Current Update on the NIS2 Implementation Process: Infringement Proceedings Against Germany
The EU's NIS2 Directive, which aims to ensure a higher level of cybersecurity, was supposed to be transposed into national law by 18 October 2024. However, Germany and 22 other EU member states have not yet fully achieved this, prompting the European Commission to initiate infringement proceedings.
Although the German government has taken legislative steps, they still await approval by the Bundestag and Bundesrat. A specific law to implement the NIS2 obligations was introduced for its first reading in October 2024. Concurrently, there is the challenge of swiftly integrating the second directive on the resilience of critical infrastructure to avoid potential legal consequences.
This delay could not only have legal ramifications for Germany but also undermine confidence in the country's cybersecurity measures. Companies must now actively engage with the requirements of the NIS2 Directive to preempt potential legal issues and security risks. Overall, the ongoing infringement proceedings underscore the urgency with which Germany must fulfil its legal obligations regarding cybersecurity to avoid both legal sanctions and security threats in the future.
In short: The NIS2 and its implementation
In the digital world, companies are increasingly confronted with cyber threats that are addressed by the NIS2 Directive. This directive aims to strengthen digital security in Europe and affects companies from all sectors. The security of IT systems plays a crucial role in protecting supply chains, which are becoming more vulnerable to cyberattacks as digitalization progresses. Investment in robust IT security measures is therefore essential to protect supply chains and increase customer confidence.
The directive, which must be implemented by 17 October 2024, contains stricter measures to increase the level of security in the EU. Companies are obliged to report relevant security incidents and register with the national authorities. A thorough analysis of their own processes and clear strategies are essential in order to fulfil the legal requirements.
The implementation of the NIS2 Directive poses a challenge due to the stricter security requirements in the EU. The German law is at an advanced stage, but the Federal Ministry of the Interior (BMI) does not expect it to be introduced on time by 17 October 2024; entry into force in the first quarter of 2025 is possible, depending on a swift parliamentary procedure. The first reading in the Bundestag took place on 11 October 2024 and the bill was referred to the Committee on Internal Affairs for further discussion.
Companies should take action at an early stage, ensure clear communication with regard to security requirements and offer training. The implementation of a business continuity strategy is crucial for dealing with cyber incidents. Last but not least, raising employee awareness is of great importance.
What do supply chains have to do with IT security?
In today's globalized world, supply chains are much more than just the physical transportation of goods. They are a complex network of processes that connect different companies and countries. But what does this have to do with IT security? Well, digitalization is having a major impact on the way supply chains are managed. Many companies are turning to technology to make their supply chains more efficient and reduce costs. IT security plays a crucial role in this.
Increasing connectivity and the use of digital tools are making supply chains more vulnerable to cyberattacks. When sensitive data is exchanged via unsecured IT systems, hackers can easily access confidential information or even paralyze the entire supply chain. It is therefore essential that companies invest in robust IT security measures to protect their supply chains from threats.
Protecting the IT infrastructure is therefore not only important for the security of company data, but also for the smooth functioning of the entire supply chain. Companies need to develop strategies to secure their digital systems, carry out regular security checks and train their employees to deal with cyber threats. This is the only way to ensure that their supply chains remain secure and stable.
It is therefore clear that the security of IT systems is closely linked to the efficiency and reliability of supply chains. By investing in state-of-the-art IT security solutions and taking a proactive approach to cyber threats, companies can not only secure their business processes, but also strengthen the trust of their customers and achieve long-term success in the global economy.
Risks and threats related to supply chains and IT security

Companies face a variety of risks and threats when it comes to the security of their supply chains and IT systems. Cyberattacks on important infrastructures and facilities can have serious consequences, both for operations and for the security of sensitive data. According to Bitkom, theft, sabotage and industrial espionage cause 206 billion euros in damage every year. Measures such as NIS2 can prevent losses and reputational damage.
According to the latest report on the state of IT security in Germany, published by the Federal Office for Information Security (BSI), the threat situation in cyberspace is more critical than ever before. The increasing networking and digitalization of our society have led to cybercrime becoming a serious problem.
Ransomware is still the biggest threat in the field of cyber attacks. Ransomware, also known as blackmail software, is a type of malicious program that restricts or prevents access to data and systems. The attackers demand a ransom to release the data. The damage can be considerable. Increasingly, both large and small organizations and government institutions are being attacked. This development means that citizens can be directly affected. Cybercriminals are becoming more professional and are increasingly using services such as "cybercrime-as-a-service". Vulnerabilities in software are increasing at an alarming rate, with over 2000 known vulnerabilities, 15% of which are critical. Generative AI presents both risks and opportunities, as it can be misused for criminal purposes. The Ukraine war has so far caused little damage from DDoS attacks, but the BSI warns of potential future challenges.
Critical infrastructure targeted: examples of serious cyberattacks
In the past, cyberattacks have repeatedly paralyzed critical infrastructures, seriously jeopardizing the security and functionality of essential systems.
A prominent example of this is the cyberattack on the Ukrainian power grid in 2015, in which hackers were able to infiltrate several power plants and leave parts of the country without electricity for hours.
Similarly, the global ransomware attack "WannaCry" in 2017 affected numerous companies and organizations, including healthcare facilities, which were paralyzed by the malware infection. Such incidents highlight the serious consequences of cyberattacks on critical infrastructures and show how important it is to protect against such threats.
In 2021, Colonial Pipeline was hit by a devastating ransomware attack that cost the company a total of $4.4 billion to pay the Darkside extortionists. This attack led to a six-day disruption in fuel supply, causing significant disruption at airports and gas stations and ultimately even triggering a state of emergency. Interestingly, the company's operational technology (OT) was not directly affected. Although billing systems were temporarily shut down, uncertainty about the extent of the attack led to production operations also being halted as a precautionary measure. This demonstrates the devastating impact of cyberattacks on businesses and highlights the importance of a robust IT security approach in the age of digital threats.
NIS2: Requirements and regulations for companies
In 2016, the European Union adopted the Network and Information Security Directive(NIS-1, Directive (EU) 2016/1148) to introduce rules on cybersecurity. This directive required EU member states to identify operators of "critical services" and introduce specific IT security measures and reporting obligations for security incidents. The implementation in national laws varied greatly in the EU countries, which led to inconsistencies. The revision of the NIS Directive (NIS2, Directive (EU) 2022/2555) is intended to create clarity.
The new version sets out key requirements for companies to ensure the security of their IT systems. Operators of critical infrastructures and important facilities must take particularly comprehensive measures for implementation. The German Federal Office for Information Security (BSI) plays an important role here by supporting companies in implementing the NIS2 requirements. Both the public and private sectors must incorporate the directive into their IT security concepts in order to ensure the security of their facilities.
What is the deadline for member states to implement the directive?
The NIS2 Directive, also known as the Network and Information Security Directive, was adopted by the European Parliament and the Council of the EU on July 6, 2016. It was published in the Official Journal of the EU on December 27, 2022 and came into force on January 16, 2023. Member states have until October 17, 2024 to implement the network and information security reforms.
What is the difference between NIS and NIS2?
While NIS (Network and Information Security) focuses on the security of network and information systems and defines the necessary measures for the prevention, detection and management of IT security incidents, NIS2 goes one step further.
The recast builds on the foundations and expands them with additional measures and requirements to ensure an even higher level of security in the Union. The Directive lays down enhanced requirements for operators of essential services and digital service providers to strengthen the resilience of their services and minimize the impact of serious IT security incidents.
There is also a significant difference in their scope of application. While NIS is mainly aimed at critical infrastructure operators, NIS2 considers a broader range of operators of essential services and digital service providers. In addition, the revision also provides for the establishment of Computer Security Incident Response Teams (CSIRTs) and a Single Point of Contact (SPoC) in the Member States to promote information sharing and cooperation.
NIS2 leads to stricter requirements for reporting and crisis response capabilities, including increased reporting obligations and more precise processes. The security regulations will be expanded to specifically address vulnerabilities, disclose security measures and evaluate risk management measures. In the event of breaches, companies face fines of up to ten million euros or two percent of turnover. Managers can be held personally liable for security breaches in the area of IT risk governance.
Overall, the update of the NIS represents a further development and strengthening of cybersecurity measures in the EU in order to effectively counter the growing threats in the digital space. The differences illustrate the continuous adaptation to new challenges and the need to improve the level of security throughout the Union.
Who is affected by NIS2?
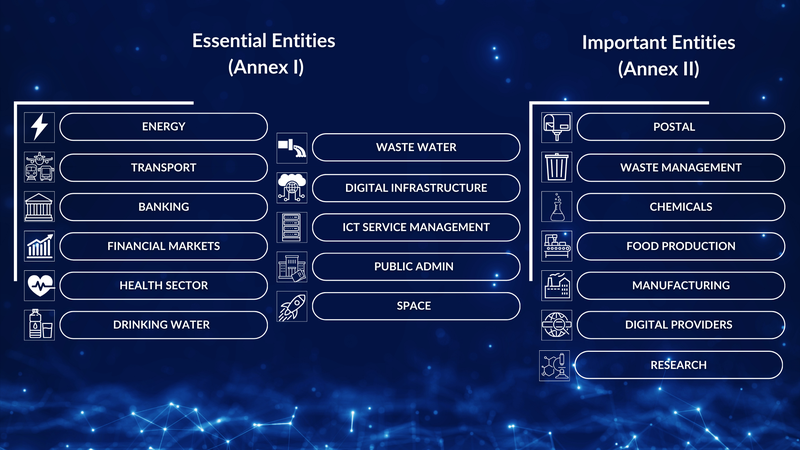
According to Art. 2 NIS2, the extent to which a facility is affected depends primarily on its size and sector. A distinction is made between "essential facilities" and "important facilities" (Art. 3). The NIS2 Directive affects facilities from 18 sectors, which are defined in more detail in Annexes I and II.
Regardless of size, other facilities are affected (see Art. 2 para. 2-4 NIS2), for example facilities such as domain registries.
Major facilities include companies operating in sectors such as energy, transportation, water, digital infrastructure, banking and finance, healthcare, public administration and space.
Important facilities include companies from sectors such as waste management, postal services, chemicals, food production, manufacturers of electronics and vehicles, digital providers and research institutions.
The application of the NIS2 requirements depends on the size of the company and its turnover. Medium-sized companies have 50 to 250 employees and a turnover of between 10 and 50 million euros. Large companies have more than 250 employees and a turnover of over 50 million euros.
The number of companies affected by the regulations is increasing significantly due to their precise criteria. As a result, cybersecurity measures are becoming mandatory for a large number of companies in Europe. It is estimated that around 30,000 companies in Germany will be subject to the requirements of the NIS2 Directive.
It is the responsibility of the companies concerned to independently check whether the directive applies to them. There is no automatic notification of applicability to the companies.
The implementation of NIS2 is an important step in arming yourself against cyber threats and ensuring security in supply chains. By consistently implementing these measures, companies can effectively counter future digital threats and protect their infrastructures.
What measures do companies need to take?
It is the responsibility of companies to take targeted measures to keep their processes and practices in line with the latest regulations and guidelines. A comprehensive analysis of the current situation and a precise evaluation of existing processes are essential in order to identify potential gaps or weaknesses. Based on these findings, clear and sustainable strategies must be developed to ensure successful implementation and compliance with legal requirements.
The management bodies monitor measures and are liable for violations (Art. 20 Para. 1). Training is mandatory and must be offered to employees (para. 2).
In accordance with Art. 21 NIS2, essential and important facilities must implement cybersecurity measures to manage risks and prevent security incidents. According to Art. 21 para. 2 lit. a-j, the measures must be based on a cross-risk approach and include the protection of IT systems, incident response, business continuity, supply chain security, security measures for the acquisition, development and maintenance of network and information systems, assessment of the effectiveness of risk management measures, cyber hygiene and training, cryptography, personnel security, access control, asset management, authentication and secure communication. In particular, in relation to security in supply chains, it is necessary to consider the specific vulnerabilities of individual direct suppliers and service providers when assessing appropriate measures, as well as the overall quality of the products and cybersecurity practices of their suppliers and service providers (see para. 3).
Define adequate measures based on a risk-based approach. By taking a thorough look at the existing risks and analyzing them accordingly, you will be able to take targeted and effective measures to protect your company from potential threats. This ensures the long-term security and stability of your company.
The reporting obligations for companies are becoming increasingly stringent: they are obliged to report relevant disruptions and incidents to the national cyber security authority without delay. In Germany, this is the Federal Office for Information Security (BSI).
According to Art. 23 para. 3 NIS2, a security incident is deemed to be significant if
(a) it has caused or is likely to cause serious disruption to the operation of services or financial loss to the entity concerned;
b) he has caused or may cause considerable material or immaterial damage to other natural or legal persons.
This takes place in a three-stage process in accordance with Art. 23 Para. 4: A preliminary report is submitted within 24 hours of the incident becoming known. A full report with an initial assessment of the incident follows within 72 hours. Finally, a detailed final report must be submitted within one month. This contains detailed descriptions of the incident, the threat, remedial measures and its cross-border effects.
In addition to the statutory reporting obligation, it is also possible to voluntarily submit reports to CSIRTs or competent authorities, in particular with regard to near-miss incidents (see Art. 30 para. 1 lit. a NIS2). This applies to significant and important facilities as well as to others, regardless of their scope of application with regard to significant incidents (see Art. 20 para. 1 lit. b NIS2).
Companies that fall under the scope of the Directive must register with the national authority. When registering, the following information must be provided in accordance with Art. 27 Para. 2 lit. a-f: Name of the entity, address and contact details (e-mail, IP address ranges, telephone number), any relevant sector and sub-sector in accordance with Annex I or II as well as a list of the EU Member States in which services are offered.
Monitoring the enforcement of NIS2
The effective monitoring and implementation of the NIS2 Directive by the member states plays a crucial role in ensuring cybersecurity in the European Union. Member states are required to designate national supervisory authorities responsible for monitoring and enforcing the rules at national level.
Furthermore, Member States shall ensure that the competent authorities effectively supervise compliance with the obligations under this Directive and take the necessary measures (Art. 31 para. 1 NIS2).
Art. 32, 33 NIS2 specify which supervisory and enforcement measures can be imposed in relation to essential and important facilities. For example, on-site inspections and external supervisory measures, including spot checks carried out by trained experts, are possible (Art. 32 para. 2 lit. a NIS2), as is the request for evidence of the implementation of cybersecurity concepts (Art. 32 para. 2 lit. g).
Member States are obliged to provide their competent authorities with appropriate enforcement powers to monitor and punish security breaches by essential entities. This includes issuing warnings, issuing binding instructions to correct errors and manage risks in the area of cybersecurity and the possibility of imposing fines in accordance with national law (Art. 32 para. 4 lit. a-i).
When enforcing measures, authorities must respect the rights of defense and take into account various factors, such as the seriousness of the infringement, duration, previous infringements, impact of damage, intent or negligence, preventive measures and cooperation with authorities (Art. 32 para. 7). The authorities must give detailed reasons for their measures and allow the affected entities a reasonable period of time to comment (Art. 32 para. 8).
The authorities can also take action at important facilities as part of subsequent supervisory measures (Art. 33 NIS2). Possible measures include on-site inspections, targeted security checks and security scans (Art. 33 para. 2). The competent authorities of the Member States have the power to take the following measures in accordance with para. 4 lit. a-h in the event of breaches of the Directive:
Issue warnings; give binding instructions to remedy deficiencies; give instructions to stop the infringing behavior and refrain from repeating it; ensure that risk management measures are complied with; inform potentially affected persons about cyber threats; give instructions to implement recommendations and set a deadline for doing so; publicly disclose infringements and impose fines in accordance with national law. The assessment is based on the same criteria as under Art. 32 para. 7 (Art. 33 para. 5).
By effectively monitoring and enforcing the NIS2 Directive, Member States are helping to strengthen the resilience of their digital space and prevent or at least minimize the impact of cyberattacks. Cooperation between member states at EU level is essential for coherent implementation and a high level of security throughout the European Single Market.
What are the sanctions for non-compliance?
Non-compliance with risk management regulations can result in high fines in accordance with Art. 34 (4) and (5): Up to EUR 10 million or 2 percent of global annual turnover for material entities and up to EUR 7 million or 1.4 percent of global annual turnover for important entities.
However, the circumstances of the individual case must be considered and criteria such as the seriousness of the infringement, the duration of the infringement and any intent or negligence must be taken into account (Artt. 32 para. 7, 34 para. 3).
Please note: According to the draft bill of the Federal Ministry of the Interior, managing directors and management bodies may be personally liable, with the fine amounting to a maximum of 2 percent of global turnover.
Status of the legislative process: current draft bill for the NIS2 Implementation Act (NIS2UmsuCG)
The EU member states are obliged to transpose the directive into national law by 17 October 2024 at the latest. However, the process of implementing the directive in the individual EU member states has been slow so far. So far, only Belgium, Croatia, Hungary, Lithuania and Latvia have successfully finalised their legislation. There are currently no plans for the European Commission to extend the deadline.
In Germany, the national law implementing the directive is being drafted by the Federal Ministry of the Interior and Home Affairs (BMI). Several draft bills have been presented since April 2023. On 24 July 2024, the Federal Cabinet adopted the first government draft of the German implementation act (NIS-2 Implementation and Cyber Security Strengthening Act - NIS2UmsuCG) after the BMI published the fourth draft bill at the end of June and it was submitted for further consultation with associations. The draft bill is currently still in the legislative process.
However, the Federal Ministry of the Interior does not expect the NIS2 Directive on improving cybersecurity to be introduced on time, which was originally planned for 17 October 2024. However, it has been indicated that it could enter into force in the first quarter of 2025, provided that the parliamentary procedure proceeds swiftly. The first reading in the German Bundestag took place on Friday, 11 October 2024, after which the bill was referred to the Committee on Internal Affairs for lead deliberation.
The content of the current draft includes important regulations and adjustments in the area of cyber security. This step is of crucial importance in order to strengthen the digital infrastructure in Germany and improve protection against cyber threats. The planned measures aim to increase the resilience of critical infrastructures and promote cooperation between the various stakeholders in this area.
Many companies are facing the challenge of meeting the legal requirements of the NIS2 Implementation Act. According to a survey by Zscaler Inc., only 14% of the European IT managers surveyed are currently prepared. Although further changes to the law are possible, selective adjustments are more likely. Discussions about the responsibility of management continue. Nevertheless, companies should not remain passive. Instead, companies should deal with the legal requirements at an early stage, review their IT security measures and close any gaps quickly, as selective rather than comprehensive changes are to be expected in the future.
The current draft bill at a glance
The new government draft of the NIS2 Implementation Act (NIS2UmsuCG) has been adopted by the Federal Cabinet and is now being dealt with in the legislative process. The government draft contains only minor substantive changes compared to the previous draft bill. Among other things, the obligations for regulated institutions of the federal administration have been concretised. The government draft makes things easier for hospitals, as they only have to submit proof of fulfilment of audit, inspection or certification obligations after five years. There are also changes to the content for companies in the energy and telecommunications sectors, which are subject to several regulations. The BSIG-E provides for extensive exceptions, as special legal requirements from the specialised laws apply. In addition, clear provisions on the liability of management and regular participation in training courses have been introduced.
The terminology differs from the European Directive. In Germany, the following grouping is used:
Particularly important facilities Section 28 (1) (Annex 1)
Pursuant to Section 28 (1) Nos. 1-4, particularly important facilities include
- Operators of critical systems,
- qualified trust service providers, top level domain name registries or DNS service providers,
- Providers of publicly accessible telecommunications services or operators of public telecommunications networks that employ at least 50 people or have an annual turnover and an annual balance sheet total of more than 10 million each,
- Other relevant companies according to Annex 1.
The latter are categorized according to sector and size; companies with more than 250 employees or a turnover of more than EUR 50 million and a balance sheet total of more than EUR 43 million fall into this category.
The various sectors include energy, transportation and traffic, finance, health, water/wastewater, digital infrastructure and space.
Important facilities Section 28 (2) (Annex 1 and 2)
Pursuant to Section 28 (2) Nos. 1-3, important institutions include trust service providers, providers of publicly accessible telecommunications services and operators of public telecommunications networks, as well as the companies listed in Annexes 1 and 2.
The relevant companies must have at least 50 employees or a turnover of more than 10 million euros and a balance sheet total of more than 10 million euros.
In medium-sized companies, the sectors listed in Annex 1 and additionally those listed in Annex 2 apply. Important sectors include postal and courier services, waste management, chemicals, food industry, manufacturing, digital services and research.
Operators of critical facilities (KRITIS operators)
KRITIS operators are identified using the KRITIS methodology. The KRITIS methodology, also known as the critical infrastructure methodology, contains a systematic procedure for identifying, assessing and ensuring the security of critical infrastructures. This methodology plays a decisive role in the risk assessment and protection of vital services and facilities in Germany.
In Germany, critical infrastructures (KRITIS) are the focus of security, as they are essential for the functioning of society. A KRITIS facility is considered as such if it exceeds a certain threshold, usually when it supplies at least 500,000 people. These facilities include important sectors such as energy supply, water supply, food, information technology and telecommunications. The safety and stability of these facilities are critical to the well-being and functioning of society. Therefore, strict security measures and regulations are established to ensure the protection and resilience of these critical infrastructures.
When implementing the NIS2 Directive, a distinction is made between two types of sectors: facility sectors in accordance with Annexes 1 and 2 and critical infrastructure sectors for critical infrastructures in accordance with Section 28 (7), which are defined by a statutory order in accordance with Section 58 (4) if the specified thresholds are exceeded. The facility sectors include both sectors of high criticality and other critical areas, which in turn are subdivided into subsectors.
Sectors of high criticalityEnergy, transportation and traffic, finance, healthcare, drinking water/wastewater, digital infrastructure, space
Other critical sectorsTransport and traffic, chemicals, research, manufacturing, digital services, food and waste disposal
Operators of critical systems are faced with increased requirements under Section 31 in order to ensure the security and integrity of their systems. Attack detection systems are therefore mandatory (Section 31 (2)).
Federal institutions (§ 29)
As part of the Implementation Act, the Federal Government is making special provisions for the protection of federal administration institutions. This therefore affects corporations, institutions and foundations under public law. Specific measures are provided for to ensure the cyber security of these institutions and to effectively counter cyberattacks. The relevant institutions are obliged under Section 29 (2) to apply some of the provisions that apply to particularly important institutions and also to fulfill their own obligations under Chapter 3.
The legal provisions specify which security standards must be met and which measures should be taken to prevent and respond to security incidents. These targeted requirements are intended to enable federal institutions to protect their IT systems and data from potential threats and strengthen Germany's digital sovereignty.
With the implementation of NIS2, the requirements for operators and facilities will change significantly. The previous KRITIS obligations essentially remain in place, but are being specified, tightened and restructured.
Particularly important and important institutions must take appropriate, proportionate and effective technical and organizational measures to protect the IT and processes of the services they provide, to avoid disruptions to availability, integrity and confidentiality and to minimize the impact of security incidents, according to Section 30 (1).
In accordance with Section 30 (1), operators are required to take into account the size of their facility, the costs of implementation, the likelihood of security incidents occurring and their severity and the social and economic consequences when assessing the risk.
Risk management measures, business continuity management (§§ 30, 31)
§ Section 30 emphasizes the importance of a holistic approach to the measures to be implemented by operators and facilities. These measures should be based on a "cross-hazard" approach and take into account European and international standards. The measures must correspond to the current state of the art and cover certain topics in accordance with Section 30 (2):
- Risk analysis and security in information technology
- Management of security incidents
- Maintenance and recovery, backup management, crisis management
- Supply chain security, security between facilities and their providers
- Security in development, procurement and maintenance, including vulnerability management
- Process for assessing the effectiveness of cyber security and risk management
- Cyber security and cyber hygiene training
- Cryptography and encryption
- Personnel security, access control and asset management
- Use of multi-factor authentication or continuous authentication
- Secure communication (voice, video and text) and secure emergency communication systems
It should be noted that the implementation of the measures in accordance with Section 30 (1) must also be documented.
Certain sectors are partially excluded from the risk management requirements in sections 30 and 31 (para. 3). Instead, sector-specific regulations are used to implement or specify corresponding measures. For example, an implementing act is to set out requirements in accordance with Section 30 (2) for areas such as DNS, TLD, cloud, data centers, CDNs, managed services, security services, online marketplaces, social networks and trust services. In accordance with Art. 21 para. 5 NIS2, the Commission has the power to adopt implementing acts by October 17, 2024. These acts serve to define technical and methodological requirements for various service providers, such as DNS providers, TLD registries, cloud computing services, data center operators and others. These requirements are then binding and take precedence.
Reporting obligations (§ 32) and duty to inform (§ 35)
There are no significant differences in the implementation of the reporting obligation, but there are specific features for KRITIS operators. Particularly important and critical facilities must report security incidents to a joint BSI and BBK reporting office. This takes place within short deadlines (24 hours) with step-by-step follow-up reports. Initial reports for serious incidents are required immediately or within 24 hours. Follow-up reports with assessment are made within 72 hours. Interim reports at the request of the BSI are also provided for. Final reports or progress reports must be submitted within one month and contain all relevant details. In addition, operators of critical systems must also provide information on the affected systems, critical services and impacts.
In the event of significant security incidents, certain institutions must inform their customers (Section 35 (1)). Sectors such as finance and insurance, IT and telecommunications are affected (Section 35 (2)). The BSI responds to reports within 24 hours where possible and can inform the public if necessary (Section 36 (1), (2)).
Registration obligation and deadlines (Sections 33, 34)
The Federal Office for Information Security (BSI) is the central point of contact for registration. It is up to each individual to identify whether they fall under the NIS2 Directive. Facilities and operators of particular importance, i.e. particularly important and critical facilities, must register with the BSI within three months, according to Section 33 (1). Operators of critical facilities are also obliged to provide further information ((para. 2)). If the registration obligation is not met, the BSI reserves the right to carry out the registration itself (para. 3).
Implementation, monitoring and training obligation for management boards (§ 38)
The management of companies must implement cybersecurity risk management measures and monitor their implementation within the organization (Section 38 (1)). The planned changes regarding the liability and responsibility of the management of affected companies could mean that they have to implement the IT risk management measures themselves. This poses potential risks to the quality of the measures. It is therefore hoped that the current draft will be reconsidered to ensure that the management is only responsible for approving and monitoring these measures.
Managing directors must also regularly attend training courses, as stipulated in Section 38 (3). Refusal to do so could lead to official prohibitions if training deadlines are not met (§ 63 Para. 9). Although fines are not provided for, external audits can be ordered to verify participation in training (§ 64).
The liability provisions have been revised and now directors are liable to the company with their private assets in the event of culpable breach of duty (Section 38 (2)). If company law provisions do not provide for any regulations, the Implementation Act applies. However, there are currently no specific liability regulations
Provision of evidence (§ 39) and examinations (§§ 63, 64)
Operators of critical systems must submit evidence of their security measures to the BSI every three years (Section 39), as was already the case with KRITIS audits.
Facilities must document measures, but may be required to carry out audits at the request of the BSI (Sections 30 (1), 63 (1), (3), (5)). The BSI selects the facilities based on risk factors (Section 63 (4)).
Supervisory and enforcement measures for particularly important facilities and important facilities (Sections 63, 64)
The competent supervisory authority is the BSI in accordance with Section 61. Certain institutions in the European Union based in Germany are subject to the territoriality principle of the BSI (Section 62). These include DNS service providers, cloud computing providers, online marketplaces and social networks. Decisions on cybersecurity risk management and the implementation of measures must be taken primarily in the Member State in which the main establishment is located (Section 62 (2)). Companies without an establishment in the EU must appoint a representative who is established in the EU (Section 62 (3)).
The far-reaching powers of the BSI with regard to supervisory and enforcement measures are set out in Sections 63 and 64 and may include audits, inspections or certifications by independent bodies.
Sanctions (§ 67)
The provisions on fines in the preliminary draft are comprehensively regulated in Section 67 and contain a precise list of administrative offenses (see paras. 1-4). Fines can be imposed for violations of the law, which vary depending on the severity of the violation (paras. 5-7).
Particularly important facilities can be fined up to ten million euros, while important facilities can be fined up to seven million euros. For other violations, fines of between two million and one hundred thousand euros can be imposed. Large companies or particularly important institutions with an annual turnover of over 500 million euros risk fines of up to 2 percent of their turnover for serious violations. Important institutions with an annual turnover of over 500 million can be fined up to 1.4 percent of their turnover.
These strict sanctions serve to ensure compliance with the regulations and to punish violations appropriately. Companies and organizations should therefore be fully familiar with the legal provisions in order to prevent possible fines and legal consequences.
NIS2 compliance: success factors and best practices
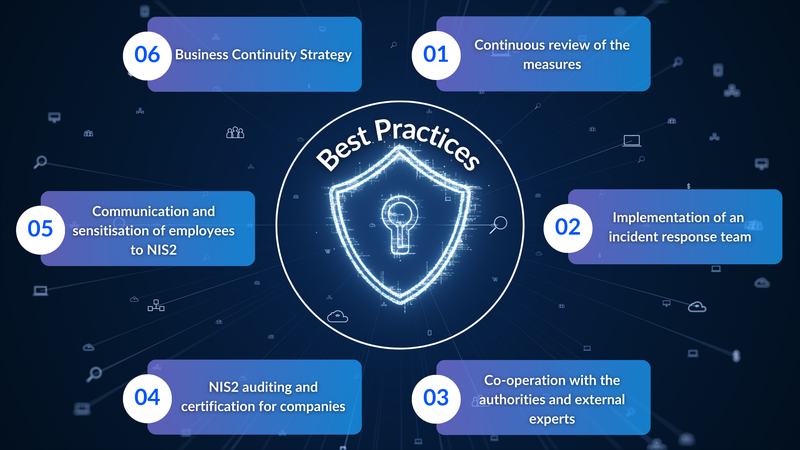
The implementation of the NIS2 Directive has a significant impact on the security of supply chains, especially for operators of critical plants and facilities. Ensuring IT security along the entire supply chain is a major challenge that companies in various industries, especially in critical infrastructure, must overcome. It is therefore of great importance to take comprehensive measures to implement the NIS2 directive in order to meet the security requirements. Success factors such as clear communication of the requirements to all stakeholders involved and the regular review and updating of the security measures taken play a key role here.
In order to implement best practices, it is essential to consistently implement security measures in all relevant sectors. Training should also be provided for employees to raise awareness of cyber security. In addition, regular audits and certifications are essential to ensure the security of IT systems.
Continuous review of the measures
It is essential that companies regularly review their security measures and adapt them as necessary to keep up with the latest technologies. Regular vulnerability scans and updates allow potential risks to be identified and remediated at an early stage. Sound cyber hygiene also requires regular security updates and the widespread implementation of multi-factor authentication methods. In this way, companies can effectively protect their data and systems and ward off potential cyber threats.
Implementation of an incident response team
The implementation of an incident response team is an important measure to be able to act effectively and professionally in the event of security incidents. A well-positioned team enables your company to respond promptly at all times and quickly contain potential threats. By setting up such a team, you signal not only to your employees, but also to your customers and business partners that security is your top priority.
Cooperation with the authorities and external experts
The successful implementation of the NIS2 directive also requires close cooperation between companies, relevant authorities such as the BSI and the Chamber of Industry and Commerce as well as other institutions involved. The integration of NIS2 into existing IT security concepts is of enormous importance and requires continuous adaptation to emerging cyber threats.
Cooperation with external experts plays an important role in ensuring a company's IT security. Through regular security checks and audits, potential vulnerabilities can be identified and remedied to effectively protect the IT infrastructure from threats. One example of this would be the integration of technical measures to detect and defend against cyber attacks using a Managed Detection & Response (MDR) service.
NIS2 auditing and certification for companies
Efficient auditing and certification in accordance with NIS2 are essential for companies to confirm and ensure the effectiveness of their cybersecurity measures. Especially in cross-sector operations and facilities, these processes play a crucial role in monitoring the proper implementation of the NIS2 directive.
It is essential for companies to ensure that all necessary requirements are met in order to achieve successful certification. The directive supports the application of European and international standards and technical specifications, such as ISO27001. Certification sends a clear signal to customers and business partners that the company's IT security is based on a high standard and therefore protects against potential security risks. Conducting an audit is a key step towards strengthening cyber security within companies.
Communication and sensitization of employees for NIS2
A key prerequisite for the successful implementation of NIS2 in companies is the targeted communication and sensitization of employees to the associated security requirements. Training and education can raise awareness of IT security and minimize risks. Well-informed employees play an essential role in the security concept, particularly in sensitive sectors such as the energy, healthcare and financial industries. This is because raising staff awareness of cyber threats, such as phishing attacks, is crucial to ensuring the security of the company.
Business Continuity Strategy
A key component of the strategy is to strengthen business continuity in the event of an attack. This includes a thorough review and optimization of backup and recovery options as well as the creation of a comprehensive emergency manual to effectively manage cyber incidents. The design and implementation of a well-thought-out emergency plan is essential to effectively counter potential cyber threats and ensure the smooth functioning of the company even in crisis situations.
Conclusion: The importance of NIS2 for a secure supply chain and IT infrastructure
The German legislator estimates that around 30,000 companies in Germany could be affected by the requirements of the Second Network and Information Security Directive (NIS2). These companies must take appropriate measures to ensure the security of their networks and information.
EU member states are making progress in transposing the NIS2 Directive into national law. The current draft bill of the NIS2 Implementation Act of June 2024 contains important regulations to strengthen cybersecurity and increase the resilience of critical infrastructures. Companies should review the legal requirements at an early stage and revise their IT security measures in order to be prepared for future changes. According to a survey, only 14% of European IT managers are currently prepared for the new regulations.
Success factors such as clear communication, regular security checks and training for employees are of great importance. The continuity of measures and the implementation of an incident response team are crucial. Cooperation with authorities and external experts is essential to protect against cyber threats. Auditing and certification to NIS2 standards are essential to verify the effectiveness of cyber security measures. An effective business continuity plan plays a central role in dealing with cyber attacks to ensure smooth business operations even in crisis situations
By consistently implementing these measures, companies can strengthen their resilience against potential cyber threats and thus ensure the integrity and confidentiality of their data. It is essential that companies act proactively and take the necessary security precautions to effectively protect themselves against cyber attacks and ensure the continuity of their business processes.
FAQ
NIS2 stands for the Directive concerning measures to ensure a high common level of security of network and information systems across the Union. This directive aims to strengthen the resilience of information systems in the EU and improve cooperation between Member States on cybersecurity. The Directive requires operators of essential and critical facilities to implement security measures to minimize the impact of cyber-attacks.
The Directive also sets out requirements for the reporting of security incidents and creates a framework for cooperation between Member States and the European Cybersecurity Agency (ENISA). NIS2 is part of the EU's efforts to strengthen cybersecurity and ensure a high level of protection for critical infrastructure and digital services.
Companies subject to the NIS2 Directive are primarily operators of essential services such as energy supply, transport, banking, financial services, healthcare, digital infrastructures and digital service providers. These companies are affected by the directive as they are classified as critical infrastructures and therefore have to meet special IT security requirements. Companies in the digital services sector such as online marketplaces, cloud computing services and search engines are also affected. It is important that these companies implement appropriate cybersecurity measures to protect the integrity, availability and confidentiality of their services.
Operational Technology (OT) in the sense of the directive refers to the systems, applications and devices used in industrial and infrastructure facilities to control operations and processes. These technologies are essential for the functionality of critical infrastructures such as energy supply, transportation and healthcare. The NIS2 directive sets out specific requirements for the security of OT systems in order to prevent potential cyberattacks and disruptions and thus ensure the stability and reliability of these systems. OT therefore includes all technological components that contribute significantly to the continuous operability of important infrastructures.
Network and Information Security (NIS2) standards play a crucial role in protecting sensitive data and digital infrastructures. In this context, the question of how NIS2 relates to Vendor Privileged Access Management (VPAM) is being raised more and more frequently. VPAM is an important part of many companies' IT security strategy as it controls and monitors third-party access to sensitive systems and data.
Implementing VPAM can help minimize potential security risks and strengthen protection against unauthorized access. By effectively managing privileged access from external providers, companies can ensure that only authorized individuals and processes can access critical resources. This makes it easier to comply with security policies and regulations, which in turn helps to meet NIS2 requirements.
The link therefore lies in a company's holistic security strategy, which aims to protect the digital infrastructure from threats and ensure the integrity and confidentiality of sensitive information. By implementing both NIS2 policies and VPAM solutions, companies can optimize their security measures and successfully defend themselves against cyberattacks.
A prominent example of a cyberattack related to Vendor Privileged Access Management (VPAM) occurred during the SolarWinds data breach in 2020, where attackers gained access to the systems of several organizations, including government agencies and large corporations, via a software update from the company. These cybercriminals were able to steal sensitive data, infiltrate networks and cause widespread damage. The incident highlights the importance of a robust security strategy, particularly in relation to the management of privileged third-party access.
The directive requires companies to take appropriate measures to protect their network and information systems and prevent cyber attacks. But what does NIS2 have to do with suppliers?
The answer to this lies in the fact that suppliers are often an important part of a company's supply chain. For example, if a supplier becomes the victim of a cyber attack, this can have a serious impact on the entire supply chain. By including suppliers in security measures, companies can ensure that their network and information systems are fully protected and that there are no vulnerabilities in the supply chain.
In addition, working with suppliers on information security can help minimize the risk of cyber-attacks for all parties involved. By setting clear guidelines and standards for their suppliers' security and conducting regular audits, companies can ensure that their supply chain is robust and resilient to threats from cyberspace.
Companies must not only implement NIS2 internally, but also work closely with their suppliers to ensure the security of the entire supply chain. This is the only way they can effectively protect themselves against cyber threats and continue their business activities undisturbed.
Critical infrastructure operators (KRITIS operators) include companies and organizations whose activities are crucial to the functioning of society and the economy. Specifically, these are operators of vital services such as energy suppliers, water utilities, hospitals, telecommunications companies and financial institutions. These operators play a central role in maintaining public order and security and in protecting the basic needs of citizens. They are therefore subject to special security requirements in order to effectively prevent and combat cyber attacks.
The Federal Office for Information Security (BSI) makes a decisive contribution to supporting operators of critical infrastructures (KRITIS). With its expertise and many years of experience in the field of IT security, the BSI offers KRITIS operators comprehensive support. This is done, for example, by providing guidelines, recommendations and best practices to strengthen cyber security in critical infrastructures.
The BSI acts as a central point of contact for operators of KRITIS and supports them in implementing measures to minimize risks and prevent crises in the area of information security. In addition, the BSI offers training courses, seminars and information events to raise awareness of IT security issues and strengthen skills in dealing with cyber threats.
The BSI has also set up Mobile Incident Response Teams (MIRT) to help operators of critical infrastructures in the event of serious cyberattacks on site. The special task forces consist of BSI cyber security experts.
Computer security incidents can have serious consequences for companies, ranging from financial losses to reputational damage. To effectively counter such threats, the NIS2 Directive has provided for the establishment or designation of so-called Computer Security Incident Response Teams (CSIRTs) by the Member States (Art. 10 NIS2). CSIRTs are specialized teams designed to respond to security incidents, analyze them and take countermeasures to minimize the impact. The exact requirements are regulated in Art. 11 NIS2.
Furthermore, a CSIRTs network should contribute to building trust between the Member States and promote rapid and effective operational cooperation between them (Art. 15 para. 1 NIS2).
The European Agency for Cybersecurity, known as ENISA (European Union Agency for Cybersecurity), plays an important role in the regulation. ENISA is an independent agency of the European Union established to support and strengthen the EU Member States in matters of IT security. ENISA works to improve the resilience of EU-wide critical infrastructures and promote cybersecurity across the Union. Its activities range from drafting policies and guidelines to supporting coordination and cooperation between Member States. Through its engagement, ENISA plays a key role in helping to better protect the EU against cyberattacks and strengthen its digital sovereignty.
The KRITIS Umbrella Act and the NIS2 Directive are closely linked and play an important role in securing critical infrastructures.
The KRITIS umbrella law focuses on resilience in the energy, water, food, health, finance and insurance, transportation and traffic, and digital infrastructure sectors. These sectors are of central importance to public life and the economy and therefore require special protection.
NIS2 (Network and Information Security), on the other hand, is a European directive that regulates cybersecurity for operators of essential services and digital service providers throughout the EU. The directive aims to strengthen EU-wide cooperation in the field of IT security and ensure a high level of security for critical infrastructures. By implementing NIS2, operators of critical infrastructure are obliged to take appropriate security precautions to prevent disruptions and attacks on their systems.
The Federal Office for Information Security (BSI) is the competent authority under NIS2, while the Federal Office of Civil Protection and Disaster Assistance (BBK) is responsible for the KRITIS Umbrella Act.
Overall, the regulations complement each other in their objectives and measures to increase security in critical infrastructures. By ensuring the protection of sensitive data and systems from cyber threats, they make a significant contribution to maintaining public security and economic prosperity.
The importance of sector-specific regulations such as the Digital Operational Resilience Act (DORA), the Energy Industry Act (EnWG) and the Telecommunications Act (TKG) plays a crucial role in connection with the NIS2. These specific laws regulate important aspects in the respective industries, from the financial sector to energy supply and telecommunications. Their requirements significantly influence the security and reliability of critical infrastructures and services, both at national and EU level. The link to NIS2 thus ensures that all relevant players in these key sectors meet the required security standards and thus guarantee effective protection against cyber threats. The harmonized implementation of sector-specific regulations such as DORA, EnWG and TKG in the context of the directive thus forms an extremely important pillar for digital resilience and security in Europe.
By implementing internationally recognized information security standards such as ISO 27001 and C5, companies can ensure a high level of protection for their digital systems. ISO 27001 sets out the requirements for an information security management system that aims to identify and assess risks and take appropriate security measures. On the other hand, the C5 standard specifically targets cloud security and provides companies with guidelines for evaluating and certifying cloud service providers. By combining these standards, organizations can strengthen their security strategy, protect themselves from cyber threats and ideally ensure compliance with NIS2.
The NIS2 Implementing Regulation (N2IR) is a comprehensive regulation that affects various providers, including DNS services, TLD name registries, cloud computing service providers and others. A draft regulation has currently been prepared by the EU Commission. This legal act provides valuable guidance, particularly in countries without clear laws, and defines specific thresholds for when security incidents are considered ‘significant’. The final feedback from the EU member states on the implementing act, which regulates the national implementation of the NIS2 Directive, was expected at the beginning of October 2024.
The N2IR sets out concrete specifications that define for service providers when a significant security incident must be reported. It also contains clear regulations on the necessary IT risk management measures that must be implemented by these providers.
The Implementing Regulation sets out specific criteria for the significance of a security incident. An incident is considered significant if it has caused or may cause financial damage of at least EUR 100,000 or 5% of the annual turnover of the affected institution.
Specific materiality thresholds apply to cloud computing providers, e.g. complete service outage for more than 10 minutes or failure to meet service levels for more than 5% of users for more than one hour. Similarly strict requirements apply to data center services and managed services providers.
The N2IR contains detailed IT risk management measures that follow international standards such as ISO 27001, but also set their own priorities such as business continuity.
The aim of this regulation is to strengthen cyber security in key areas and to respond appropriately to security incidents. Companies in these sectors should therefore take a close look at the provisions to ensure that they meet the prescribed security standards and can respond appropriately to potential threats.
